Project Description
Drammer is a new attack that exploits the Rowhammer hardware vulnerability on Android devices. It allows attackers to take control over your mobile device by hiding it in a malicious app that requires no permissions. Practically all devices are possibly vulnerable and must wait for a fix from Google in order to be patched. Drammer has the potential to put millions of users at risk, especially when combined with existing attack vectors like Stagefright or BAndroid.
Drammer is the first Android root exploit that relies on no software vulnerability and is an instance of the Flip Feng Shui exploitation technique. After Dedup Est Machina and Flip Feng Shui, Drammer is our group’s third in a series of Rowhammer exploitation research. Our Drammer exploit and companion Drammer test app (see below) were implemented in collaboration with the University of California, Santa Barbara.
Rowhammer
is a hardware bug that allows attackers to manipulate data in memory without accessing it. More specifically, by reading many times from a specific memory location, somewhere else in memory a bit may flip (a one becomes a zero, or a zero becomes a one). Our work is the first to show that Rowhammer is possible on mobile, ARM-based hardware.
Flip Feng Shui
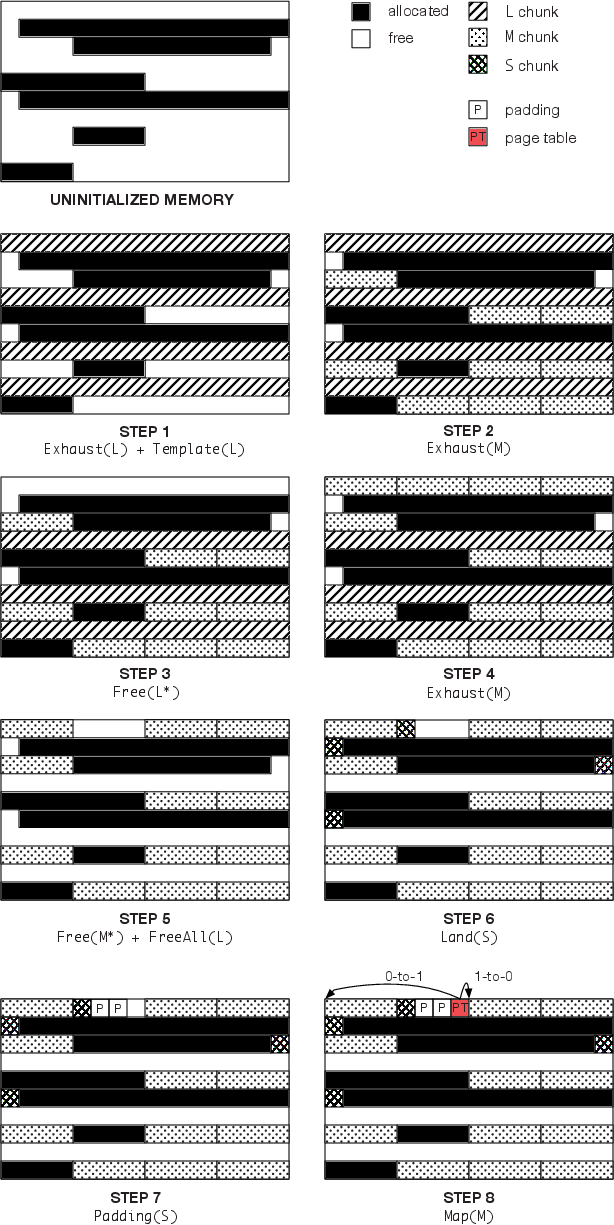
or FFS is a technique that allows for reliable exploitation of a hardware vulnerability (e.g., Rowhammer) by combining it with a memory massaging primitive (to land sensitive data on a vulnerable location). Drammer is the first to show that such deterministic Rowhammer exploitation is possible without relying on fancy memory management features. Although we focus mainly on mobile devices, this makes that Drammer comes with a wider impact; allowing FFS attacks without memory deduplication, for example.
Papers
Drammer Test App
We developed an Android app – not yet in Google Play, but available directly – to test your device for the Rowhammer bug. The app uses a native binary for which we also released the source code. After a successful run, the app uploads anonymized output. We will use this to get a better understanding of how widespread the Rowhammer bug is. Of course, you can opt out of sharing results.
Please note the following:
- Currently, when finished its hammering session, the app does not give you a nice popup that tells you whether you are vulnerable or not. We will try to add this as soon as possible. Meanwhile, you can easily spot induced bit flips by glancing over the output and looking for the obvious keyword FLIP.
- Your phone might still be vulnerable, even if the app detected zero flips! There are two main reasons for this. First, our current implementation of address selection is conservative: we recently discovered that the current code is only hammering half of the rows on a Nexus 5. On your device, the DRAM geometry might be different enough for our app to completely fail selecting addresses for double-sided rowhammer. Second, the app may only have tested a very small fraction of your DRAM. Ideally, a single run takes at least an hour and scans a couple hundred of MB. The current code already tries to free as much memory as possible to hammer (affected by the aggressiveness factor), but there are probably better ways of doing this.
Hammertime simulator
We developed Hammertime, an open-source Rowhammer simulator – available on github – to foster further research on the Rowhammer bug. The simulator allows researchers and practitioners to simulate hardware bit flips in software, using bit-flip patterns (or fliptables) from a large set of DRAM chips. We plan to integrate bit-flip patterns we observed with Drammer on ARM soon.
Statistics
Not every phone is susceptible for the Rowhammer bug. For our paper, we tested 27 devices and were able to flip bits on 18 of them. In the table below, you can find statistics on devices that were tested so far.
| Model | #devices | #vulnerable |
|---|---|---|
| ARMv7 (32-bit) devices | ||
| LG Nexus 4 | 1 | 1 |
| LG Nexus 5 | 15 | 12 |
| Motorola Moto G (2013) | 1 | 1 |
| Motorola Moto G (2014) | 1 | 1 |
| OnePlus One | 2 | 2 |
| Samsung Galaxy S4 | 1 | 1 |
| Samsung Galaxy S5 | 2 | 1 |
| ARMv8 (64-bit) devices | ||
| HTC Desire 510 | 1 | 0 |
| Lenovo K3 Note | 1 | 0 |
| LG G4 | 1 | 1 |
| LG Nexus 5X | 1 | 0 |
| Samsung Galaxy S6 | 1 | 0 |
| Xiaomi Mi 4i | 1 | 0 |
We encourage everybody to try our Drammer test app and help figuring out how widespread mobile Rowhammer is. We expect, for example, that devices equipped with LPDDR4 are less vulnerable. This is because the LPDDR4 standard includes optional hardware support for the so-called target row refresh mitigation.
Demos
The first demo video shows Drammer against an unrooted LG Nexus 5 running Android 6.0.1 with the latest security patches (as of October 5, 2016).
https://www.youtube.com/embed/x6hL-obNhAw
Our second video shows a successful end-to-end exploit chain of Stagefright (to get remote code execution) in combination with Drammer (to gain root privileges). By tricking the victim into opening a malicious URL, an attacker gains remote shell access to the vulnerable device. Since the exploited mediaserver is not running with root-privileges, however, he still cannot access /sdcard, for example. The attacker then launches the Drammer exploit which does give him full control over the device.
https://www.youtube.com/embed/0pV-Q9Q5s4Q
Note that we did not write our own Stagefright exploit, but gratefully used Metaphor from NorthBit. You can find our Stagefright shellcode here (requires SELinux to be disabled). Second, in the video, we upgrade our netcat remote shell after successful Stagefright exploitation so that we can use raw input and use tab-completion. The C source and Makefile for this pty-shell are also available online.
In the Dutch television show Universiteit van Nederland, we applied the Stagefright + Drammer attack to hack a phone of somebody in the audience.
Technical Walkthrough
Drammer presents two novel contributions: 1) being able to do Rowhammer on mobile devices, and 2) doing deterministic Rowhammer exploitation without relying on fancy memory management features. What follows is a technical summary of our paper, but only if you’re interested.
Reception
Drammer gathered extensive media coverage. The responsible disclosure process was started on July 25. In conjunction with Google, we did not publicly disclose any details about Drammer prior to the CCS conference in Vienna. Google informed their partners about this issue on October 3, 2016 and provided a patch for it in their November Android Security Bulletin.
Ultimately, CVE-2016-6728 was assigned to this issue. Our bug report and Proof-of-Concept received a reward from the Android Security Reward Program. The vulnerability was marked as Critical by Google.
Note that, although Google’s patch round from November complicates our attack, it does not eradicate it. We hope to see a more sophisticated fix soon.
Frequently Asked Questions
Why the name Drammer?
Drammer (or actually DRAMMER) may be short for Deterministic RowhAMMER. However, it is also a combination of the words DRoid and hAMMER and also has the part DRAM in it. Finally, in Dutch, Drammer means nag or pusher. Take your pick!
How wide-spread is Mobile Rowhammer? How can I check whether my phone is vulnerable?
We don’t know yet, but you can help us finding out. We developed a Drammer test app for you to play with.
I have a phone with LPDDR4 memory. Am I safe against Drammer attacks?
Again, we don’t know. Chances are that your DRAM comes with the Target Row Refresh (TRR) mitigation, which makes it harder – but still not impossible, in theory – to induce bit flips. Moreover, TRR for LPDDR4 is optional, so your DRAM manufacturer may have decided to drop this technique and leave you vulnerable.
Will my device receive a patch to stop Drammer attacks?
This depends on your device’s vendor. We expect that Google’s first patch will get back ported to recent devices. Since a more comprehensive solution requires fundamental kernel changes, however, it is unlikely that such patch ever reaches existing devices. Ultimately, it is up to your device vendor to decide whether or not they will adopt proposed fixes.
I have an older phone and am unlikely to get any updates. Now what?
If you’re lucky, your device is not vulnerable for Rowhammer – did we mention our Drammer test app? If it is, you’ll have to be careful about what apps you install. Make sure that you disable the allow app installation from unknown sources feature to get the best protection.
I constantly monitor installed apps for suspicious events. Am I safe against Drammer attacks?
You’re probably hinting at recent techniques like ANVIL, [BHUSA’15], or the mitigation proposed by the Linux kernel developers. By monitoring cache misses, such mitigations can only detect Rowhammer attacks that execute many cache flushes. Unfortunately, Drammer hammers uncached (DMA) memory and thus never triggers a cache miss. In fact, we expect that no existing anomaly detection system can stop Drammer.
I want to use Drammer to root my phone. Where can I download the exploit code?
You cannot. We decided to not (yet) release the exploit. We did open source our templating code, however.
Acknowledgements
This work was supported by the Netherlands Organisation for Scientific Research through grants NWO 639.023.309 VICI “Dowsing” and NWO CSI-DHS 628.001.021, by the European Commission through under programme GA No. 644571 (SHARCS), programme GA No. 644052 (HECTOR), and programme GA No. 610436 (MATTHEW), by the ONR under Award No. N00014-15-1-2948 and Award No. N00014-17-1-2897, by the NSF under Award No. CNS-1408632, by DARPA under agreement No. FA8750-15-2-0084, and by Google through a Security, Privacy and Anti-Abuse award. The public artifacts reflect only the authors’ view. The funding agencies are not responsible for any use that may be made of the information they contain.